
Essentially what it
means is
that the functionality protected by this test is often
taken
advantage by unscrupulous programmers or scripters. While the
host is Ok
with possibly an individual performing whatever the associated action
say a
dozen times, the same host may not be prepared to handle circumstances
where an
automated sequence performs the same action hundreds, thousands or
even
potentially millions of times. This type of test aims to
slow down or prevent automated use of the host feature, by at the very
least pausing the automation at the point of the test to require human
intervention.
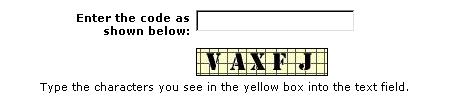
I recently revamped PayPal's version of the test (above) for a new
server that tracks
unwanted
scripted use of the PayPal system. As
scripting is
detected a new style and hopefully much more acurate CAPTCHA test is
issued to stop the automation. OCR programs are known to crack
older style and we
did not
want to encourage the scripting writers to integrate OCR code in there
scripts continuing unabated. I'm rather pleased with my work,
however I understand
that it may
be tougher to answer (even for a human) and that for the traditional
places at least
for the moment, the legacy CAPTCHA will continue to serve as guardian.
I won't explain how one could appear to be hacking into the PayPal
system just
to
provoke the anti-scripting code to issue a CAPTCHA of the new
design. I
did however discover a defect that would expose the new design.
With the combination where 1) the old
traditional style key should be generated, and 2) the system believes
it is
under attack (i.e. the CAPTCHA defense itself is being tampered) the
new CAPTCHA design will be displayed instead of the above style. NICETRY
is our message to those that may tamper with the system. Its not
really an Easter
egg
feature as the display of the new style in the old place is
unintentional, but there is a simple way to get the following PayPal
reply directly out of the current server with only a standard web
browser. This feature
will be cleaned up in a later release of the website, but assuming that
all
works well our more exuberant clients (a.k.a. fraudsters and
hackers) may
continue to
see this new design ( with VAXFJ or whatever the randomized key is
generated) long into the future.

